We Been Codin' Like Rabbits.
It's a new year and we've come out of the rabbit hole to release a few tools and scripts that have assisted us in recent adventures. These tools should all be considered beta and works in progress but worth sharing to error on the side of helping others. In addition, we are making an effort to quickly get our Python 2 scripts upgraded to Python 3 due to the sun-setting . Below you will find more information about the new tools and how to use them. Please contribute, provide feedback, and reach out to us anytime at lostrabbitlabs@gmail.com.
About LRL Tools:
The scripts in our repo are meant to supplement existing industry tools, and have a focus on 'Full Spectrum Teaming' (used by teams & rabbits of all colors). The tools were designed to produce rapid result sets which include high amounts of actionable information, in easy to use formats. We share them with the hopes of helping the community evolve tradecraft through providing coding examples, showing usage, and discussing ways to improve them and used techniques going forward. ;)
WisQuas - https://github.com/LostRabbitLabs/wisquas
A simple 'URL Revealer' (fast and lightweight scanner, enumerator, fingerprinter, fuzzer, assessor, and collector). Assists with finding vulnerabilities, anomalies, unique servers, available files/dirs, HTTP methods, and accessible web containers, in addition to auto-decoding headers and cookies.
- Lang: Python2 - tldextract, urlparse, colorama, base64, binascii, codecs, ssl
- Purpose: Penetration Testing / URL Scanner
- Input: Provide one (1) URL with protocol
- Output: Color coded console output
Example command: ./wisquas.py -1 "http://www.lost-rabbit.com/"
More information: New Tool Release: WisQuas
GimmeCookies - https://github.com/LostRabbitLabs/gimmecookies
Python3 script to generate CSV output files from domain-wide crawl for digital assets (like cookies!). Cookies can be further explored with another LRL tool - AnomalousCookie.
- Lang: Python3 - sys, socket, subprocess, requests & Sublist3r
- Purpose: Penetration Testing / Digital Asset Management
- Input: Provide one (1) domain name
- Output: CSV output of headers & cookies along with discovered subdomains
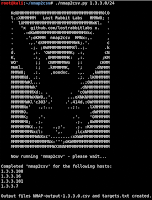
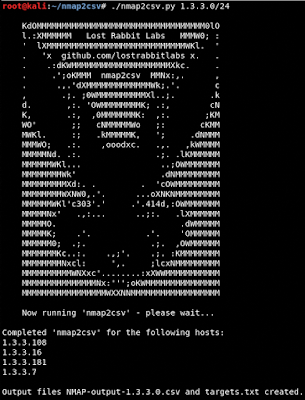
nmap2csv - https://github.com/LostRabbitLabs/nmap2csv
A wrapper for Nmap that outputs port scan results to a CSV file (and an output 'targets.txt' file for use with 'grabbit').
- Lang: Python3 - uses python-nmap
- Purpose: Penetration Testing / Network Scanner
- Input: Network or IP Address in CIDR format
- Output: CSV output of Nmap scan results & 'grabbit target' file
grabbit - https://github.com/LostRabbitLabs/grabbit
Grabbit Like A Rabbit! Grabbit is a Python/Selenium based fuzzy screenshotter (png format). Provide a 'targets.txt' file with host:port (1 per line) and grabbit will provide service info and screenshots for all discovered hosts/ports.
- Lang: Python2 - requests, socket, sys, pyvirtualdisplay, selemium, os
- Purpose: Penetration Testing / Fuzzy Screenshotter
- Input: Provide targets file with one (1) 'host:serviceport' per line
- Output: 2 directories with PNG screenshots and TXT output of requests
domaindoxer - https://github.com/LostRabbitLabs/domaindoxer
Quickly gather information around a provided 'domain name' in the areas of leaked code/docs/info, malware associations, pastebin dumps, public containers, and general OSINT.
wabbit - https://github.com/LostRabbitLabs/wabbit
- Lang: Python3 - uses google search library
- Purpose: OSINT - Find Data Leakage around a given domain name
- Input: Provide one (1) domain name
- Output: URL results from google on the CLI
wabbit - https://github.com/LostRabbitLabs/wabbit
(W)hois (A)sn (B)locklist (B)ulk (I)nquiry (T)ool - Create a CSV output file of Domain name and ASN Whois, and Blocklist status information for multiple domains. Uses URLVOID, SiteAdvisor, Fortiguard, and optionally Google Safe Browsing API4 (requires your own api key).
- Lang: Python3 - whois, IPWhois, bs4, pysafebrowsing
- Purpose: OSINT - Bulk Whois/Blocklist Lookup
- Input: List of targets in a file
- Output: CSV output of results (1 domain per row)
Thank you to everyone in the community and hacker family who has inspired, contributed, supported, and dedicated themselves to making our world (the physical and virtual) a better place. No matter what color your team is...remember that we are truly on the same team and in this together!
Happy New Year & Happy Hunting!
-- the Lost Rabbits --